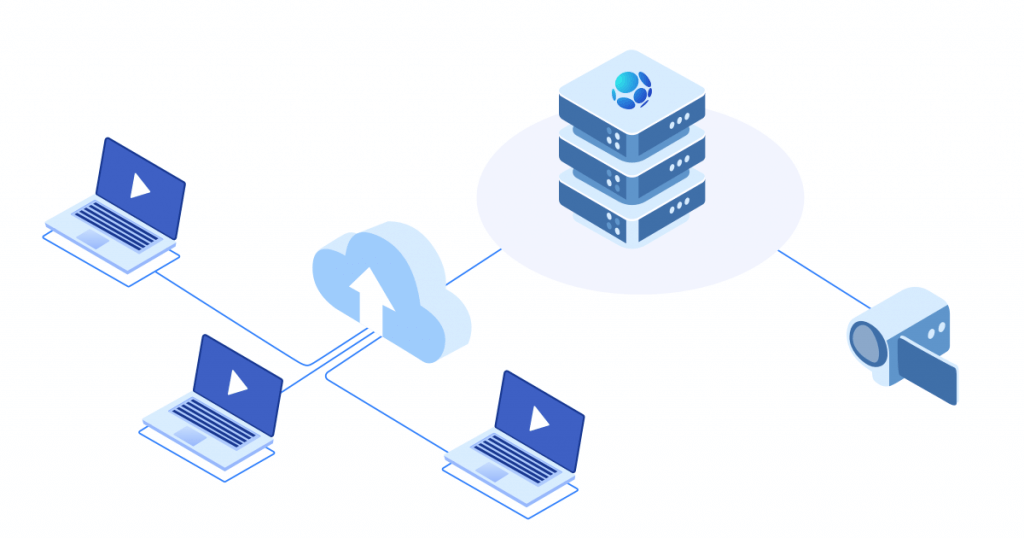
Five main CDN security threats in 2020: forewarned is forearmed
- Hosting News, Knowledge Base
- November 10, 2020

Guide to CDN Providers 2020: Prices Comparison
Previous Post